I haven’t posted in a while but I’ve decided to write some longer form entries of larger projects I’ve worked on. First up is Producteev. I was hired in 2011 as a Windows desktop engineer to make their first Windows application, and this is my story about that.
Blog
Installation issues on Ubuntu 20.04 LTS
Last week I was given a free secondhand HP 17-x051nr, an inexpensive Intel i3-based laptop. For the price of a $30 replacement battery and an SSD I had on-hand I now have a newish laptop to use.
Getting the 20.04 LTS release of Ubuntu running on it had some issues, so here’s a guide to working around these and getting the latest Ubuntu LTS installed.
Symptoms
The installation screen would become unresponsive around the Installation type screen where I would select how I wanted to format my drive. I was able to open a terminal and run top and I noticed that systemd takes up 100% CPU usage. Eventually the whole system would freeze and leaving it overnight to finish installing didn’t help.
Switching over to the Try Ubuntu option wasn’t much better. I would see a TTY screen with flashing error messages that were scrolling too fast to read and it would eventually lock up entirely.
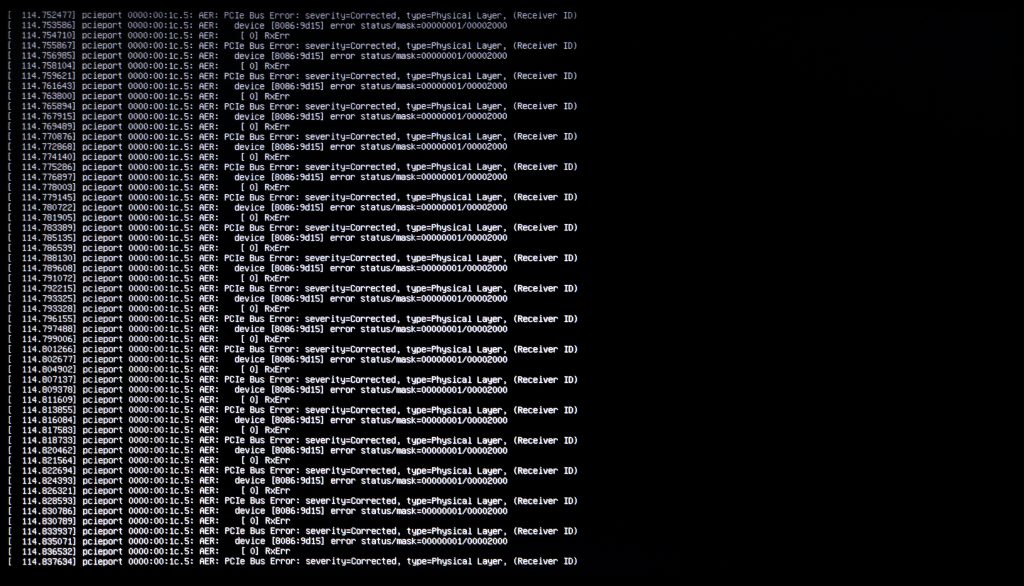
pcieport 0000:00:1c.5: AER: PCIe Bus Error: severity=Corrected, type=Physical Layer, (Receiver ID) pcieport 0000:00:1c.5: device [8086:9d15] error status/mask=00000001/00002000 pcieport 0000:00:1c.5: [ 0] RxErr
This laptop was released in August, 2016, which is not that old for a PC. It should still run a new Ubuntu version just fine. It turns out this is a relatively common issue on laptops.
The Fix
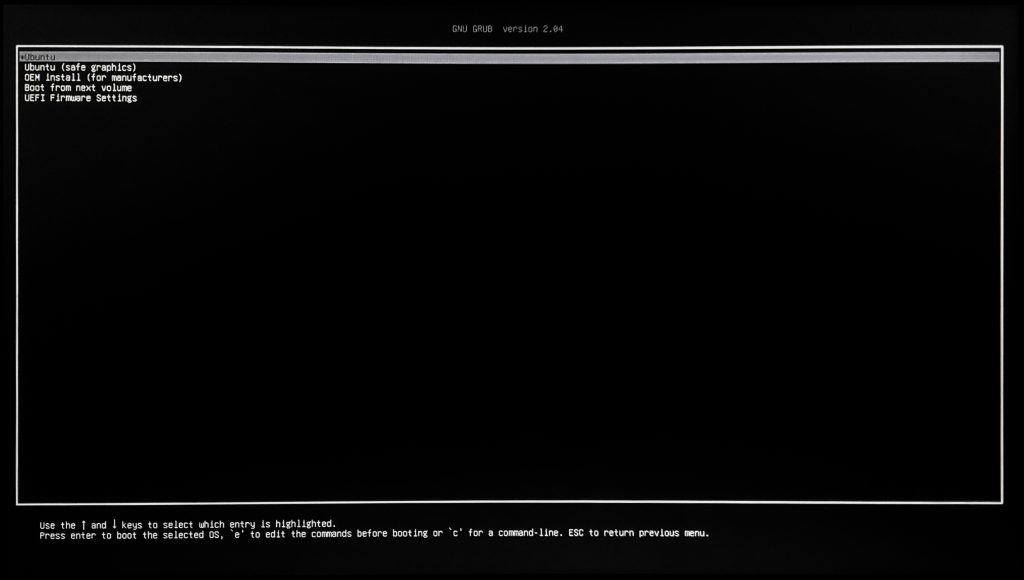
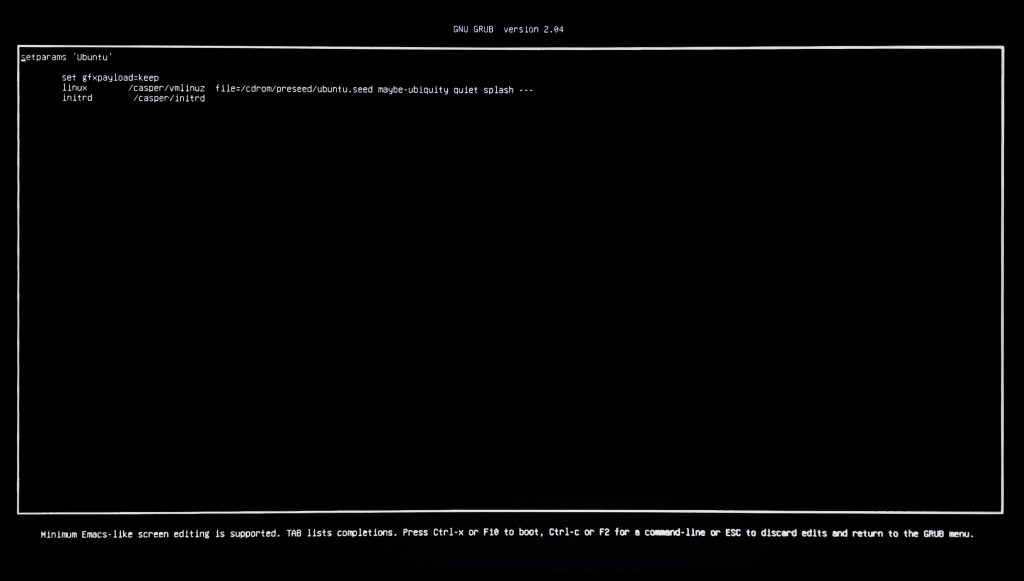
The first step is to change the GRUB boot line for the live Linux boot media. When the GRUB menu opens up press ‘e’ to edit the launch commands.
You’ll want to add pcie_aspm=off following directly after the splash parameter on the linux line.
Once you’re able to boot use the Try Ubuntu option. Maybe the regular installer works for some people but I wasn’t able to get it to run. You should not see any PCI express errors flashing on the screen at this point. Once the desktop environment opens, launch the installer from there. Do not connect to WiFi, and do not install any extra packages because it will cause the installation to fail. (I.e., use the Normal Installation option, but don’t install the third party software and do not download updates. You can do both of these later.)
As a side-note, I would recommend keeping UEFI enabled.
Once you finish the installation you may reboot and remove the installation medium. You’ll be getting PCIe errors again but it will eventually boot. Log in and use your favorite editor to open up /etc/default/grub as admin. We want to change this line:
GRUB_CMDLINE_LINUX_DEFAULT="quiet splash"
to this:
GRUB_CMDLINE_LINUX_DEFAULT="quiet splash pcie_aspm=off"
Save and then update GRUB:
sudo update-grub
I would recommend rebooting after this. Everything should be working smoothly now. Please drop a comment if this helps or if you’re still having issues.
Thoughts after a year of daily Japanese practice
Last year I picked something that I had to stick to for a year no matter how hard it got. Today I hit day 400.
I would encourage virtually everyone to set aside some daily time for a habit that you can one day master, starting small and expanding it only as you grow more comfortable. It doesn’t matter what you do, as long as you care about it. These are my thoughts on learning a new language.

In my high school days I had developed a passing interest in Japanese. I didn’t get very far into vocabulary or grammar, but I learned the Kana (ひらがなとカタカナ,) which count for two of the three Japanese writing forms. Kana is comprised of 46 letters for each set, but common Japanese writing also uses an additional 2,000+ Kanji. I didn’t get that far. Learning a new language requires an intense amount of study and it’s easy to get overwhelmed if you consider it all at once.
Years have passed since my high school days and common teaching methods have improved. I really recommend spaced repetition apps like Duolingo or Memrise which use a flash card style approach that allow you to study in short sprints. I think this is the key to getting hooked. In fact, 15 minute blocks of study seem to be the perfect, bite-sized duration to target for new language learners. Good lessons will make you want to do more, and grueling lessons won’t be long enough to set a bad tone for your day. Little by little your skills compound. Once a stronger habit takes hold your study time will pass by in a flash. It took around 6 months for my overall mindset to switch from “just putting in my time” to actively working to gain mastery, and I naturally adjusted to longer and more frequent blocks of study.

You should be prepared to have some rough days. On bad days you can just fulfill your minimum obligation then set it aside. Remember that the discomfort of new lessons will pass and these will soon become easy and familiar landmarks in your mind. Consider this when you review old topics as well since those were all foreign to you at one point. Expect challenge but don’t worry; and time will take care of the hard parts.
You will eventually want to go deeper with your studies. I recommend you develop good principles to facilitate this: be patient with yourself, and make the best use of your time, (i.e., use time actively instead of passively.) This doesn’t mean to intentionally seek struggle. You want to learn the easiest way that you can, of course, but understand that there’s rarely a shortcut or perfect system. This applies to every practice.
My learning resources for Japanese
Duolingo, Wanikani, 8020japanese, and Tofugu are great for most learners. I recommend to go the cheap or free route when starting out with most new hobbies and these sites have a lot of free resources. There’s also a nearly unlimited amount of Japanese learning YouTube channels. You’ll want to spend some time finding teachers or communities that you resonate with. Treat it like you’re applying for an apprenticeship and you have to find someone that keeps your interest.
Takeaways
Being able to talk to my favorite Japanese photographers through Instagram this year felt like an amazing milestone for me. I’m also proud to feel more comfortable with screwing up and the vulnerability of the process. What a way to learn about yourself, and it starts out with such a small commitment.
Whatever you want to do for a year, I hope you not only stick to it, but do it consistently, and have a wonderful time with it. You never know where it could take you.
Ganbatte!
Added a now page
This is an old idea that I liked from Derek Sivers. I’m going to keep it up to date with stuff that I’m working on, rather than announcing it in separate posts. Focus shifts pretty rapidly over here but I really only want to announce the finished stuff.
New resource page — artists
Some of my work is inspired by the people I follow closely, and since I think others can benefit from them as well I’ve made a page with a small selection of artists I follow.
It takes a long time to go through my follow list and write descriptions on Instagram and YouTube so I kept the list short for now. I will be adding more to it later.
Tools List
A quick announcement, I’ve added a Tools page to document helpful software that I’ve collected over the years.